LITE
Adversary Tradecraft.
Made Usable.
Stop extracting TTPs manually. Analyse adversary and malware behavior instantly.
We answer
The Questions Other Platforms Can't.
Many say they align to MITRE ATT&CK but...
- Where is the evidence for this technique?
- How often does it appear across reporting?
- Can I pivot across reports without rebuilding context?
YOUR ADVERSARY TRADECRAFT RESEARCH PLATFORM
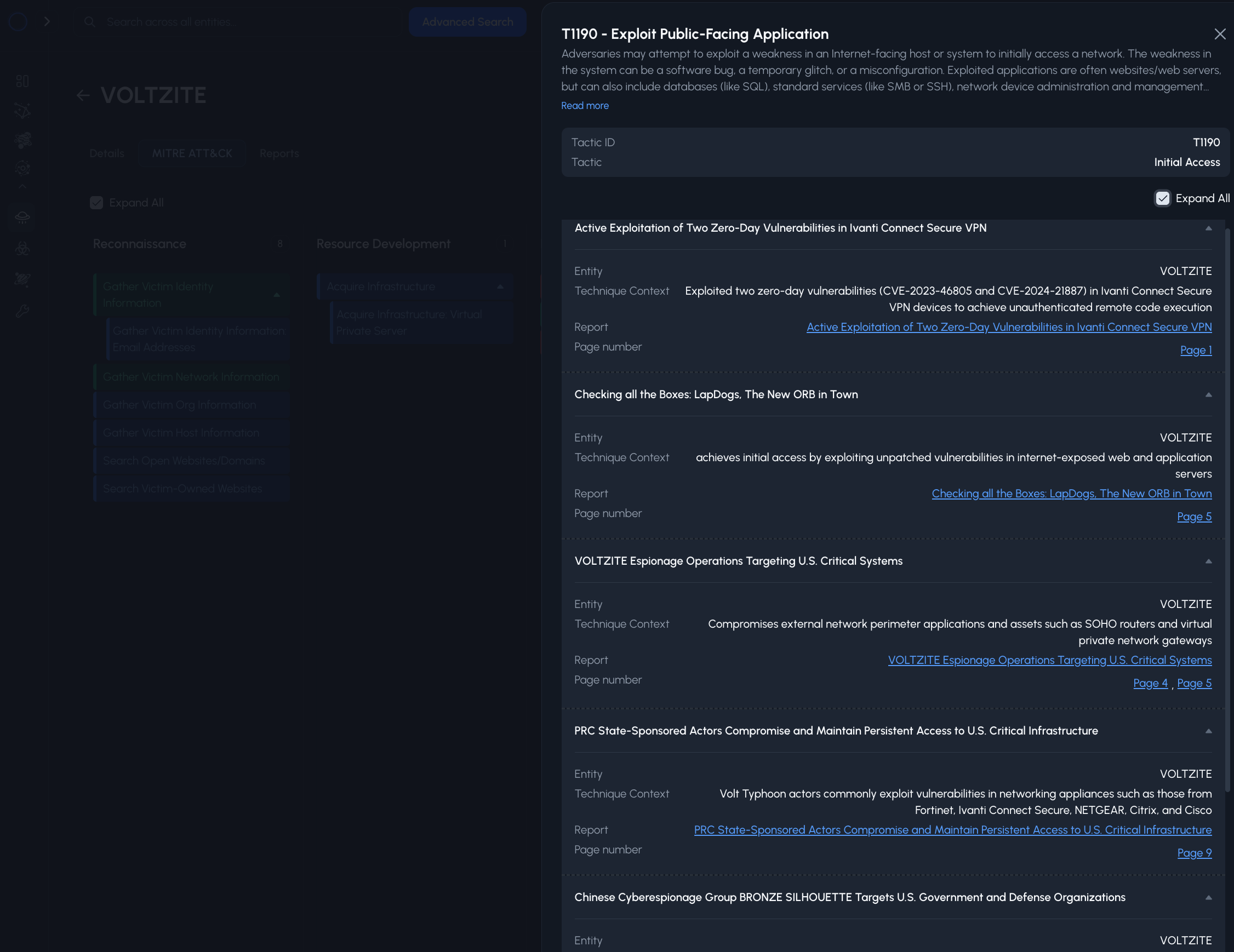
We've done it! We've managed to extract EVERY adversary tradecraft context from EVERY REPORT, and mapped it to MITRE ATT&CK.
Don't wast time searching for where ATT&CK is mentioned in reports. Go directly to the evidence with clickable page references for each technique.

GET TO KNOW YOUR ADVERSARY
Do you want to know what attack behaviors are most frequently used by your adversaries?
View the frequency of techniques and sub-techniques used by adversaries, and inform your decitions.

GO DEEP, REAL DEEP INTO ADVERSARY TRADECRAFT
Go from entity level details, directly to the source report with one click.
Each technique in our MITRE ATT&CK heatmaps allow you to go to the source reports instantly.
Alternatively, technique context is provided on the spot so you can decide what to do next.
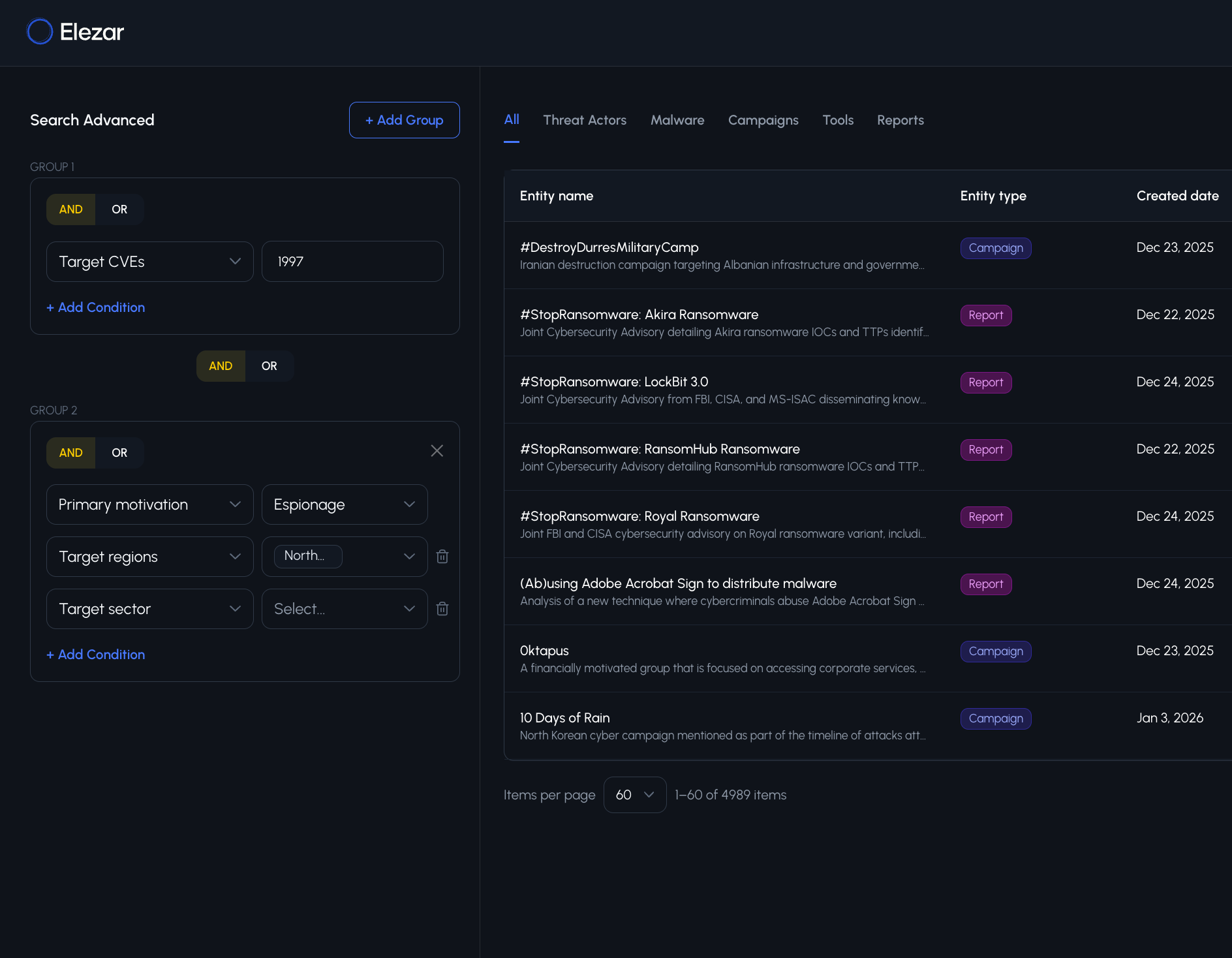
ADVANCED SEARCH CAPABILTIES
Dive deeper into our collected data and find exactly what you're looking for.
Search attributes such as motivation, sophistication, sponsor, target technology, target technology vendors and more!
Boolean enabled search empowers you to do more.
Take Adversary Tradecraft Research to another level.
Turn Intelligence Into Threat-Informed Outcomes.
Continuously prioritize what matters and execute with confidence.